Mysterious Computer Hacker Icon. White and Grey. Isolated on Black Stock Vector - Illustration of hack, icon: 112854761

Complete White Hat Hacker Certification Bundle Is Up For A Pay What You Want Offer For A Limited Period Of Time - Avail Now

Ethical Hacking as Explained by White Hat Hackers - Cyber Security Solutions, Compliance, and Consulting Services - IT Security




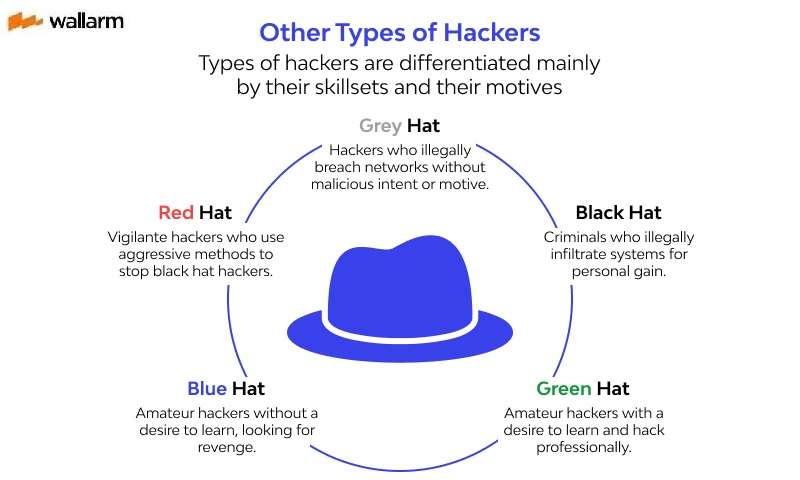





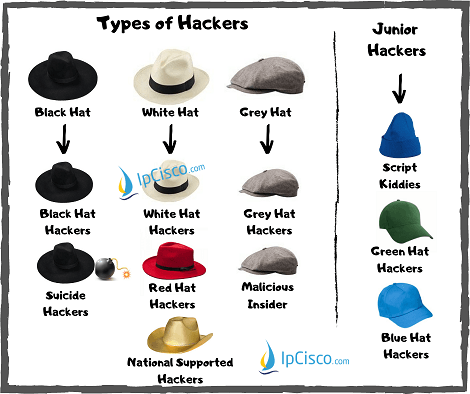


![White hacker - Stock Photo [55329507] - PIXTA White hacker - Stock Photo [55329507] - PIXTA](https://en.pimg.jp/055/329/507/1/55329507.jpg)





